Locks and Security News: your weekly locks and security industry newsletter
10th April 2024 Issue no. 700
Your industry news - first
We strongly recommend viewing Locks and Security News full size in your web browser. Click our masthead above to visit our website version.
Relay attacks on cars now in the public domain
 Three researchers from the system security group at ETH Zurich in Switzerland were able to break into 10 vehicles made by 8 manufacturers and drive them away by intercepting and relaying signals from the cars to their smart keys.
Three researchers from the system security group at ETH Zurich in Switzerland were able to break into 10 vehicles made by 8 manufacturers and drive them away by intercepting and relaying signals from the cars to their smart keys.
ETH Zurich’s researchers said that the materials for the wireless attack cost as little as $100, depending on the electronic components used. The same equipment was used on all brands.
ETH Zurich has publically released information from their recent research into a low cost generic relay attack on cars. The concept of a relay attack is not new and has already featured heavily in the press across Europe and the USA. But this is the first time that details of such a practical realisation of the theory have been released.
SBD has been working confidentially with a number of clients on the progression of defences against relay attack. Our recently published white paper, 'How are thieves stealing modern vehicles?' highlights the operation of such devices and our research, 'Relay Attack - A Real Threat to Smart Key Security?' explains what thieves are currently doing and how this weakness is likely to be exploited.
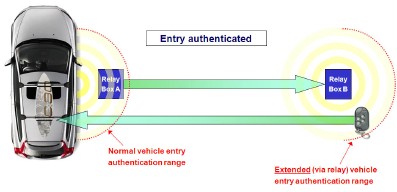
A relay attack is performed through the use of a paired set of radio devices. These are used to capture the signals emitted by the vehicle and the replies from the Smart Key, and extend their range so that the key and vehicle believe that they are within the authorised operation area. In doing so, a thief is able to enter the vehicle and start the engine, disarming all conventional onboard security without having the original key and without alerting the owner of the vehicle. Relay attacks can typically operate over a range of 100 to 1,000 metres, depending on the equipment used and on the environmental conditions.
Using equipment costing less than $1000 the researchers from ETH Zurich were able to create two versions of the attack - one wired and one wireless - and verified their success on a number of test vehicles. The principle operation behind the two attacks was the same with the only difference being that the wireless connection allows a true covert attack to be conducted and represents how a thief would actually use the technology to steal vehicles.
The attacks were successful on 10 vehicles from 8 different manufacturers. The researchers were able to access and drive away each of the models by relaying the original signal from the car to the remote key, rather than attempting to break the cryptography. The key point to note from the research is the generic scope of the weakness. The attacks were proven successful on a number of vehicles from several different manufacturers. Individually targeted tools were not needed and SBD's research shows that this attack method can be duplicated on most vehicles using smart key technology.
Further solidifying their presence in the public domain, this research will be presented in February at the Network and Distributed System Security Symposium.
SBD has the knowledge and technical expertise to be able to offer in depth consultancy opportunities to vehicle manufacturers and suppliers to help develop solutions with which to overcome the developing problem of relay attack. We will carefully monitor further reactions to this release of information, especially from security approval organisations. For more information, email [email protected]
26th January 2011








